
Photo by Lukas Blazek on Unsplash
Generating time-based one-time passwords in Privileged Session Manager WebApp Connectors
Table of contents
Edit: After conversing with a contact, this requires version 13.0 of the PSM no matter the version of the Secure Web Application Connectors Framework!
Edit 2: This is not officially supported but there exists an enhancement request you can vote on.
Like possible with CyberArk Central Policy Manager plugins for Web applications, you can generate time-based one-time passwords (TOTP) as part of a Privileged Session Manager (PSM) connector.
The Web Application CPM Plugin Framework enables you to generate a TOTP as part of the WebFormFields but this functionality is not advertised for PSM connectors as part of its Secure Web Application Connectors Framework. Despite this, it is still possible.
Furthermore, we can generate a TOTP with a secret stored as a Logon Account instead of storing the secret as part of the PSM connector's WebFormFields.
Generating a TOTP in WebFormFields
Generating a TOTP for a Webapp PSM connector is done the same way as with a CPM plugin for a Webapp. You can copy and paste right out of Example 3 in the Web Form Fields section of the CPM plugin for Web applications documentation:

Launching the PSM connector, the OTP is generated and injected successfully:

But hardcoding the TOTP secret as shown in the example doesn't make sense as the secret will be different for each account and the secret itself should be kept as secure as the password.
The TOTP secret as a Logon Account
The best way to securely store the TOTP secret is to onboard it as an account. Afterward, we will use that account as the Logon Account from which we will retrieve the TOTP secret.
The account the TOTP secret is onboarded with can have any platform, address, username, etc. CPM management can be disabled unless you have a CPM plugin that can rotate the TOTP secret itself.
After linking the TOTP secret as a Logon Account, we can tweak our WebFormFields to generate the TOTP using the Logon Account's password using the {logonaccount\password} property instead of a hardcoded value:

Before we test our new PSM connector, we need to add LogonAccount to the Supported Capabilities under the Target Settings of the PSM connector:

If we neglect to add LogonAccount, then the Logon Account's properties and password will not be available to the PSM connector and we receive an error:
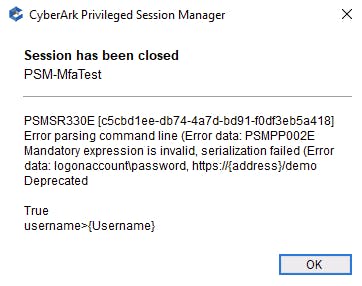
With the WebFormFields updated and the capability added, the PSM connector launches, generates a TOTP based on the secret stored in the password of the Logon Account, and injects it successfully:
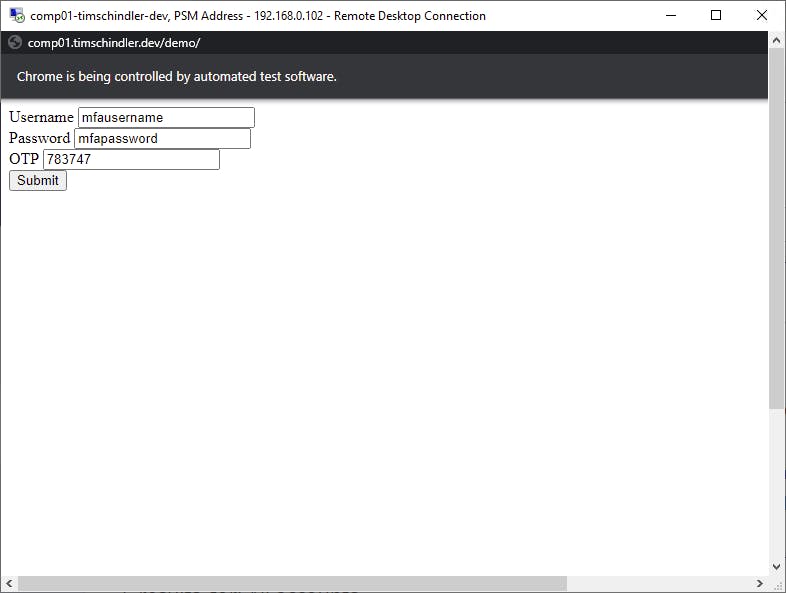
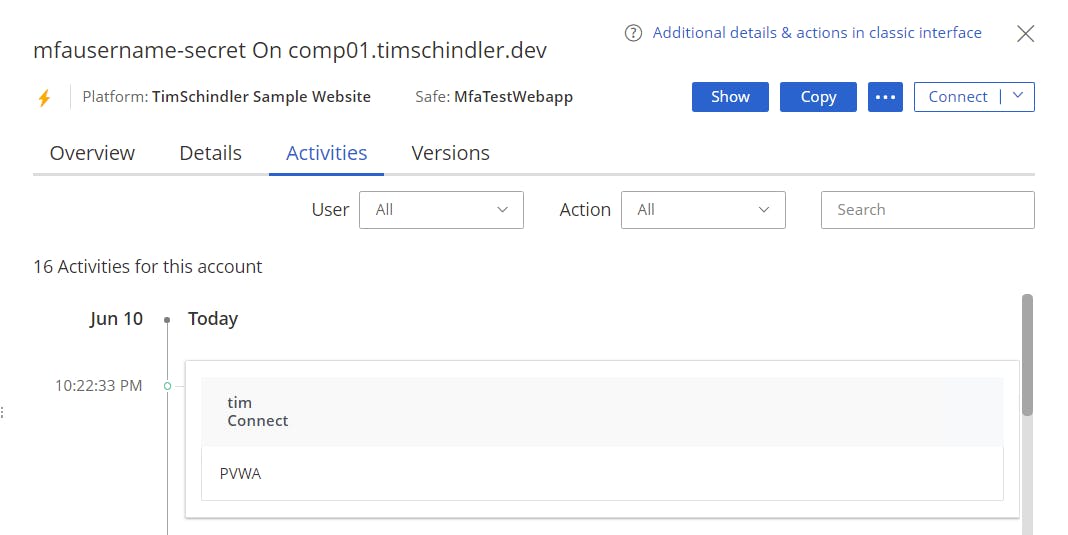
We see the username of the Logon Account in the details of the PSM Connect activity:

And we see a Connect in the activities of the Logon Account:
It's not clear why this PSM connector functionality is undocumented by CyberArk. Maybe it is not supported or the documentation was simply overlooked?
Either way, just like generating a TOTP as part of a CPM plugin may be needed in some scenarios, the same goes for PSM connectors.

